How are the Elections Administered?
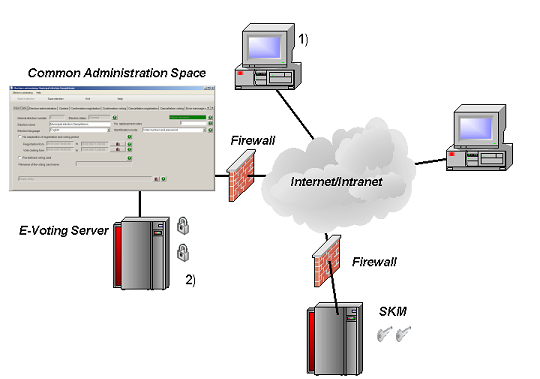
(1) Election committee members virtually meet in the Common Administration Space, simultaneously define the election parameters, load the roll, check and release the election.
(2) The public keys for ballot encryption are provided by the committee members, the private keys are retained in the SKM only to be retrived by the respective committee member.
The Common Administration Space enables the election committee to enter and check all relevant parameters. Checking functions are provided to check integrity of the data. On release of a constituency/election the relevant parameters cannot be manipulated (Step 1).
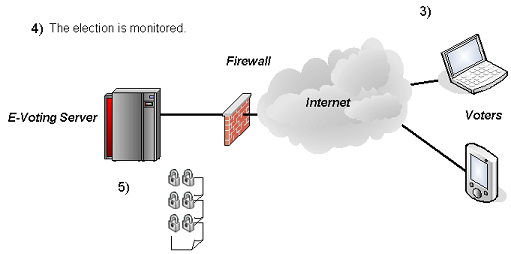
(3) Once the election has been released and the dates have arrived, voters may register and vote according to the parameters specified using Java-enabled Web browsers.
(4) The election is monitored.
(5) Votes are stored encrypted and inaccessible to the server administration
Upon release, the committee defines the opening quorum for the ballot box and each member generates a private/public key pair, where the public key is used to encrypt the vote in the voting client; each private key remains in the Key Server and can only be released by the respective committee member. Hence, neither the system administration of the Election Server nor any single committee member is able to manipulate the ballots (Steps 2 - 5).
EVOTE offers extensive monitoring tools both for the election committee and for the system administration. All sessions are traced (without corrupting voting secrecy!) and system administration is notified of suspicious activities.
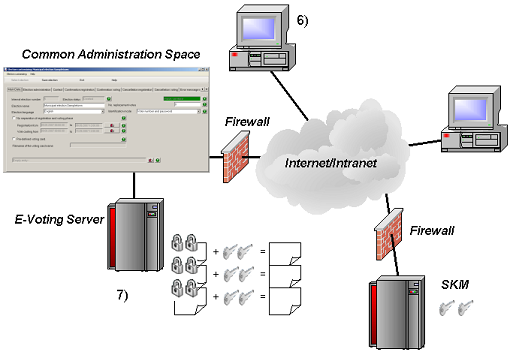
(6) After the election, the defined quorum of election committee member provide their private keys again simultaneously using the Common Administration Space.
(7) After the election, the pre-defined quorum of committee members meet in the Administration Space, provide their private keys and the ballots are opened and counted.


