Application Scenario I: Document Management in Organizations
This scenario is a standard situation in many business processes, whether it be in the public sector, banking or legal information systems. Let us explore the electronic submission of tenders (Electronic Procurement) as an example:
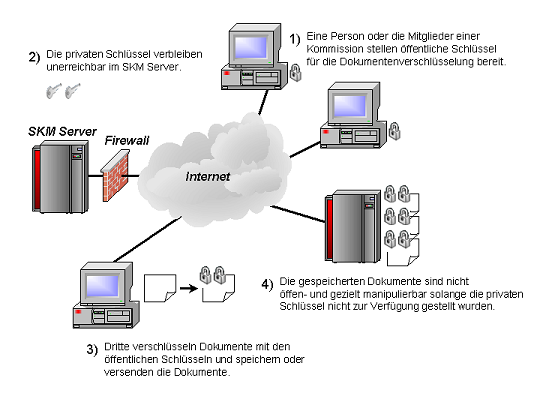
The committee members responsible for the tender generate key pairs in the SKM Server, where the public key is made available to potential bidders and the private key remains unknown to be later reconstructed by the SKM Server (Steps 1 and 2). Bidders submitting their tenders use the public keys to encrypt their tender documents.
Note: document encryption and possible document con¬catenation with SHA-1 hashing can easily be implemented with the ready-made functions of the SKM Requestor Crypto Library (Steps 3 and 4).
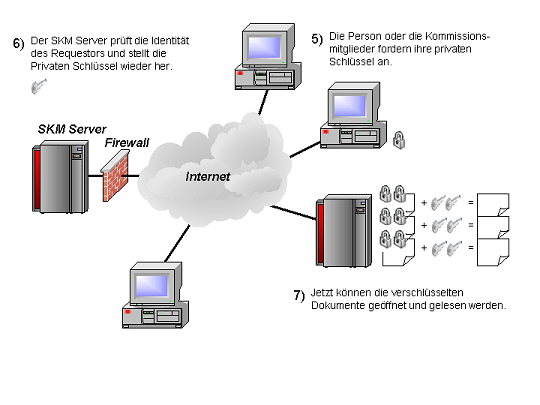
When the submission period expires, the committee members request their private keys from the SKM Server. Only the person or application originally requesting the key generation may retrieve the key (Steps 5 to 6). Once all private keys have been provided, the encrypted bids are opened (Step 7).
Application Scenario II: Electronic Voting (e-voting)
A similar scenario is used in e-voting.
The Secure Key Manager is responsible for providing the security necessary to prevent the tampering of votes. This is achieved by encrypting the ballot sheet with the public keys of the election committee members before the ballot sheet is submitted to the election server (Steps 3 and 4). In doing so, neither the system administration of the Election Server nor any single committee member is able to manipulate the ballots.
In using the SKM, each committee member requests generation of a private/public key pair and a public key is issued to each member. The private key remains unknown. The only person to request its reconstruction is the committee member who requested its generation and each committee member has to expressly reconstruct the respective private key.
After vote casting has been terminated, the members of the election committee retrieve their respective keys and jointly provide the information necessary to open the ballot (Steps 5 to 7 above).
Majority Decisions in a Committee
In either scenario, majority decisions may be implemented. For example, 3 out of 5 committee members may access a document or may open an electronic ballot box. The defined quorum may not be altered later and may not be manipulated, for instance, by a database administrator manually changing the database content.

